From KnowB4.com —
By ROGER GRIMES
Many small and mid-sized companies use Intuit’s very popular QuickBooks program. They usually start out using its easy-to-use base accounting program and then the QuickBooks program aggressively pushes other complimentary features, including QuickBooks Payment. This add-on features the ability to send customers’ invoices via email. The payee can click on a “Review and pay” button in the email to pay the invoice. It used to be a free, but less mature, feature years ago, but these days, it costs extra. Still, if you are using QuickBooks for your accounting, the ability to generate, send, receive and electronically track invoices all in one place is a pretty easy sell. Intuit touts QuickBooks’ ability to send email invoices here.
Unfortunately, phishing criminals are using QuickBooks’ popularity to send business email compromise (BEC) scams. The emails appear as if they are coming from a legitimate vendor using QuickBooks, but if the potential victim takes the bait, the invoice they pay will be to the scammer. Worse, the payment request can require that the payee use ACH (automated clearing house) method, which requires the payee to input their bank account details. So, if the victim falls for the scam, the criminal now has their bank account information. Not good.
Note: Some other QuickBooks scam warnings will tell you that QuickBooks will never ask for your ACH or banking details. This is not completely true. QuickBooks, the company and its support staff, never will, but QuickBooks email payment requests often do.
Legitimate QuickBooks Payment Email Example
Here is what a legitimate QuickBooks payment request looks like. I recently received it for a company who cleaned my boat.
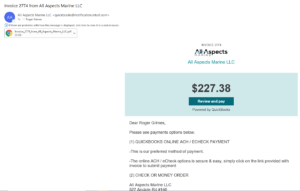
The fake QuickBooks’ payment emails look very much the same. The only difference is it might be from a company you do not recognize (Social Engineering Red Flag #1). There’s a second clue that I’ll cover more below.
When I hovered over the “Review and pay” button to see what URL was underlying it, I get this:
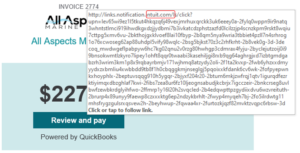
Note that the link points to the intuit.com domain, same domain that the email originated from. That is a big clue that this email payment request is legit.
When I looked at the email’s message header, I get further clues that this email is from really from Intuit. The first (at the bottom of the header) “Received:” line, which reveals what email server sent the message is shown below:
![]()
Note: If you want to learn how to examine email headers to extract useful information, see my one-hour webinar on the topic.
The sending email server claims to be from the intuit.com domain.
Is it really from intuit.com or is it just pretending to be Intuit.com?
Glad you asked. Luckily, this email contains SPF, DKIM and DMARC information in the message header, which will let an email receiver know if the sending email domain being claimed (in this case, intuit.com) is really where the email came from.
If you want to learn more about SPF, DKIM and DMARC, see my one-hour webinar on the topic.
Here is the relevant SPF, DKIM and DMARC header information from the legitimate email.
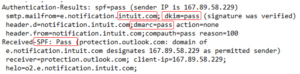
It shows that the email passed the SPF, DKIM and DMARC checks. This email invoice really was sent from intuit.com.
Email invoices sent from QuickBooks arrive from intuit.com. The scam ones usually do not. The real QuickBooks invoices arrive from Intuit.com and not the QuickBooks-using vendor who uses it because Intuit set it up that way. They want to maintain control, update it when needed and to count uses and other related statistics. The invoices are created and generated from the originating vendor’s QuickBooks instance, but the actual invoice is sent by Intuit.com, not the vendor.
QuickBooks scam invoices could arrive from Intuit.com if the scammer bought QuickBooks and bought and used the real QuickBooks invoicing feature. But as soon as a victim complained to Intuit, the fraudulent instance would be shutdown (I hope). Either way, I have not seen a scam QuickBooks invoice actually originate from intuit.com. So, if you see a QuickBooks invoice and it truly originates from intuit.com, then it is a strong clue that the invoice is really from who it says it is from. This does not have to always be true (i.e., a legitimate QuickBooks customer could be compromised), but it is a pretty reliable indicator of legitimacy.
Note: A scammer could also compromise a real QuickBooks user and then use their legitimate QuickBooks instance to send fraudulent invoicing, but that would take changing the QuickBook’s user’s banking information, which would likely then be quickly noticed as soon as the first victim complained to the compromised sender.
Fake QuickBooks Payment Invoice Example
Here is an example of a fake QuickBooks invoicing scam email sent to me by a customer (and censured to avoid identifying the customer and other innocently involved business name).
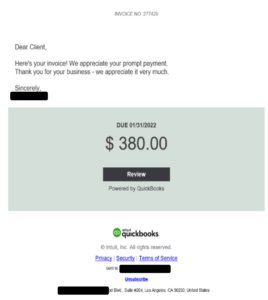
On first pass, it looks fairly close to what a legitimate email might look like. One of the first clues that something is wrong is that the greeting says, “Dear Client”. The real QuickBooks email was addressed to me by name. It also contained a PDF-version of an invoice, and that invoice contained an itemized list of work done for me, so I could verify that it was work I was expecting to be invoiced for. An attacker could create a fake PDF invoice attachment, and even try to include malware or a malicious link in it, but it would likely not contain an itemized list of EXPECTED work recognized by the potential victim. If it did have an itemized list of items, it was supposedly invoicing for, I am sure the list would be very generic.
But the real kicker in positively identifying this second email as a fraudulent email was in its email message header. The first clue was the originating email server.
![]()
It said emsd4.com. Well, that is not intuit.com, so we know it is not a legitimate QuickBooks invoice. Done. Fraud. Phishing attempt.
Then I wondered, did it really come from emsd4.com? I checked for SPF, DKIM and DMARC records in the header:
![]()
So, both SPF and DKIM pass (it didn’t have DMARC enabled). The email really did come from emsd4.com, whatever that domain is. I could never find out what emsd4.com domain was used for, but as best as I could tell, it was a domain running on an email service running on Amazon’s AWS (a frequent host of cybercriminals because of their free to very cheap resources). Emsd4.com could be a legitimate domain and email service being used illegitimately, like Gmail.com and Outlook.com, are thousands of times a day. But when I plugged in the domain name to MXToolbox’s blacklist checking tool, this came up:
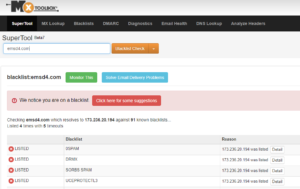
Usually when I put in a phishing domain I’ve personally verified as sending malicious content, I sadly find out that no one has previously reported the involved domain to a single blacklist. Not the case here. It has been reported to at least four or more different blacklists, including the same IP address.
So, others have felt the need to report emsd4.com for previous nefarious activities. Not a good sign.
My customer had a strong suspicion this was a scam even before they got into the email headers and sent it to me. And they did what we all should do when we receive suspicious requests: They contacted the involved sender using alternate, legitimate, method using the vendor’s direct website, and inquired about the unexpected bill. This is what they asked and learned:
Turns out the third party that was involved as the supposed original sender had nothing to do with email. From their quick reply I would even guess that this isn’t the first time someone has inquired about an unexpected, fraudulent, invoice pretending to be from them. Even without being an email forensics expert, all it took to figure out that the request was fraudulent was a single contact to the involved vendor. The whole world would be a better place if we all did that one simple thing first.
Other QuickBooks Scams
Note, I covered a particular type of QuickBooks involved scam above. There are dozens of others, completely unrelated to this type, including:
- Fraudulent calls pretending to be QuickBooks support agents asking you to renew the license
- Fraudulent emails claiming to be QuickBooks’ emergency security updates
- Emails about supposed pricing discounts
Intuit has a list of known Intuit-branded phishing scams here.
Conclusion
Millions of people and businesses use QuickBooks to run their business with tons of customers used to receiving and paying QuickBooks-generated email invoices. By attackers sending out QuickBooks phishing emails, there is going to be some percentage of receivers who are likely to fall for the scam. If it is an unexpected QuickBooks-generated email invoice, check the email header to see if it originated from intuit.com or not. Or contact the involved purported vendor using a trusted alternate method to verify before paying. I think we are going to see a lot more QuickBooks scams in the future.
Contact KM&M CPAs
If you have questions regarding your business or individual taxes, contact the experts at Kleshinski, Morrison & Morris CPAs. Reach us by phone at 419-756-3211, by email sent to kmm@kmmcpas.com, or by filling out our contact form on this site at this link.

